- Home
- Policies
- Policy Index
- Cybersecurity
Cybersecurity

Who we are: METI’s Role in Cybersecurity
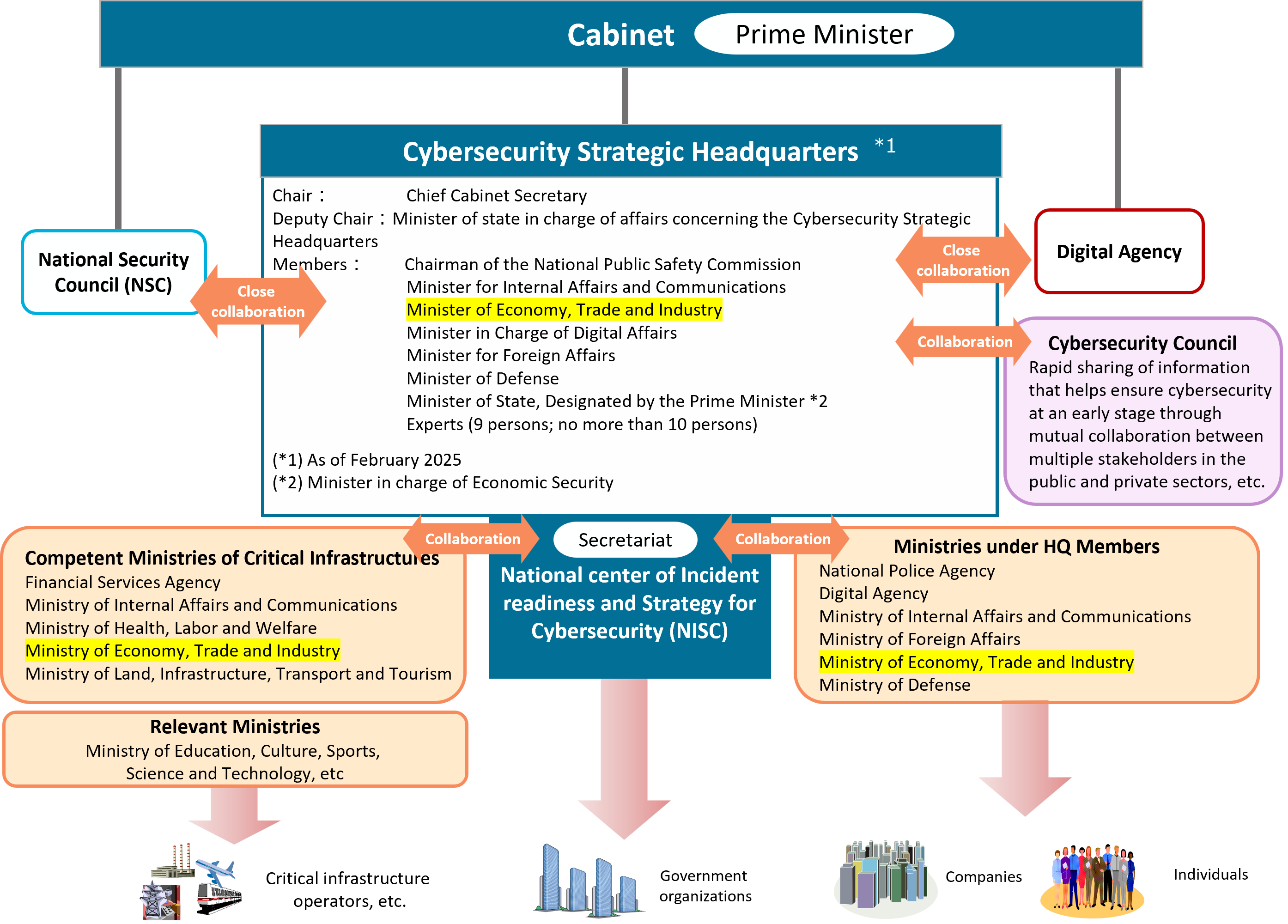
In Japan, each ministry is responsible for cyber security policies in their respective areas, and overall coordination of cybersecurity policy is conducted by NISC (National center of Incident readiness and Strategy for Cybersecurity) under the Cybersecurity Strategic Headquarters.
METI’s mission is to improve cybersecurity measures in the industrial sector.
Our Policies
- Cybersecurity measures for companies
- Research and Development
- Promoting Cyber Industry
- Critical Infrastructure
Gas, Electric power, Petroleum,
Credit, Chemical
Press Release
- JP-US-EU Industrial Control Systems Cybersecurity Week for the Indo-Pacific Region Held (November 25, 2025)
- Memorandum Signed on Mutual Recognition of Labeling Scheme based on Japan Cyber-Security Technical Assessment Requirements (JC-STAR) and the UK Product Security and Telecommunications Infrastructure (PSTI) Act (November 6, 2025)
- Guidelines on the Roles Expected of Cyber Infrastructure Providers (draft) Compiled in Japanese and English Versions (October 30, 2025)
- OT Security Guidelines for Semiconductor Device Factories Compiled in Japanese and English Versions (Octover 24, 2025)
- Joint Statement on the Global Cybersecurity Labelling Initiative (GCLI) Released (October 23, 2025)
- 18th ASEAN-Japan Cybersecurity Policy Meeting Held (October 16, 2025)
- METI Jointly Signs International Guidance on a Shared Vision of Software Bill of Materials (SBOM) for Cybersecurity with National Cybersecurity Office (NCO) (September 4, 2025)
- (Draft) OT Security Guidelines for Semiconductor Device Factories Compiled in Japanese and English Versions (June 27, 2025)
- Cybersecurity Guidelines for Energy Resource Aggregation Business Revised (May 22, 2025)
- Study Group for Promoting the Development of Cybersecurity Talent Compiles and Announces Its Final Report (May 14, 2025)
- Guide Introducing Specific Procedures and Examples Formulated to Help Small and Medium-Sized Manufacturers Ensure the Security of Their Factories (April 11, 2025)
- Launch of IoT Product Security Labeling Scheme (JC-STAR) (March 25, 2025)
For all companies
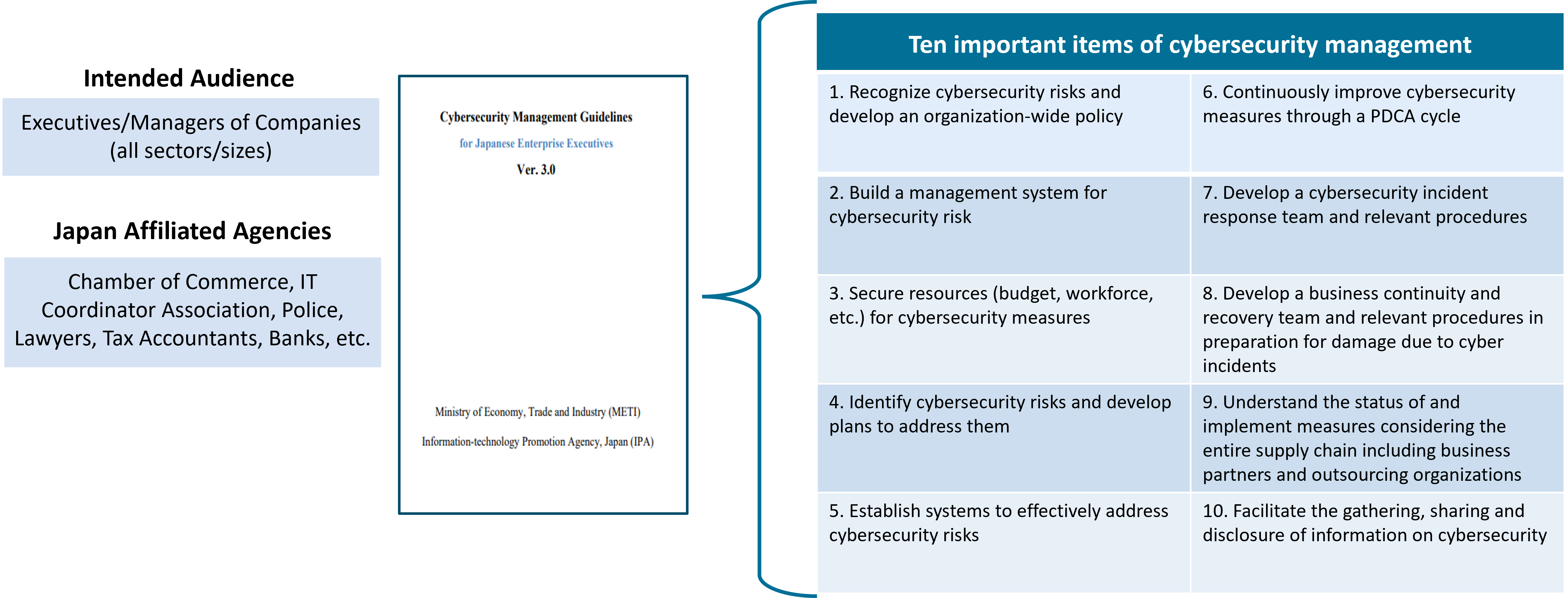
Cybersecurity Management Guidelines
A guideline on company management for all sectors and sizes, as management must be involved with implementing cybersecurity measures before cyberattacks and cyber incidents occur.
For SMEs
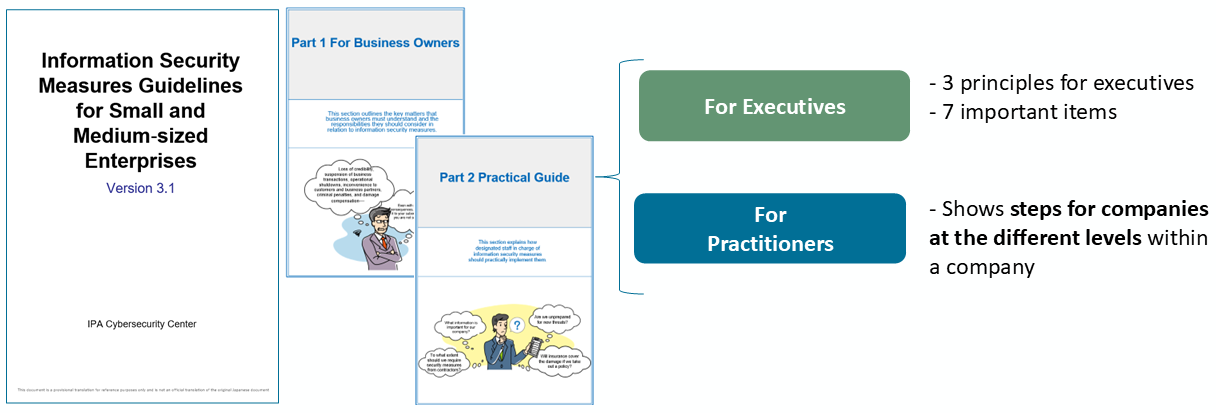
Information Security Measures Guidelines for Small and Medium sized Enterprises
The 'Information Security Measures Guidelines for Small and Medium-sized Enterprises' is a guideline that summarizes the necessity of security measures, the risks associated with not implementing these measures, and the actions that should be taken to protect companies from these risks. It is designed to help small and medium-sized enterprises, as well as those companies that are just beginning to implement security measures, understand the key points to consider when addressing cybersecurity measures.
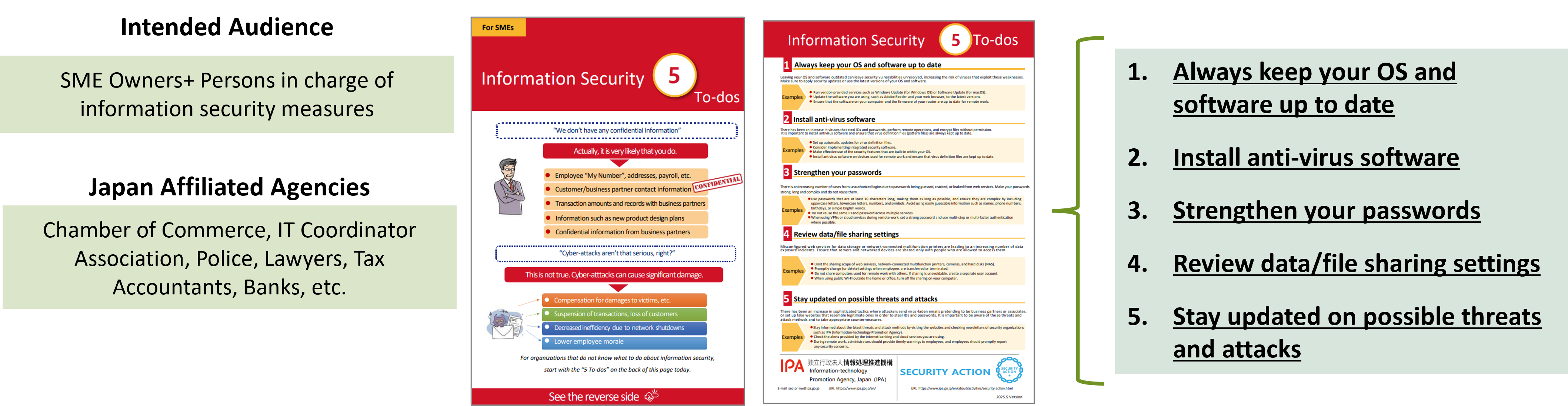
Information Security 5 To-dos (First Step)
The Information Security 5 To-dos summarizes five essential measures that should be implemented regardless of the size of the company.
5-Minute Self-Assessment (Second Step)
A Self-Assessment Questionnaire sheet to easily identify the information security measures your organization should prioritize, particularly for SME owners and practitioners.

For certain sectors
Guidelines for Factory Systems
A guideline for factories to protect data and equipment when in operation, as cyber attacks targeting factories are increasing in number and sophistication. Specifically targeted for ICS and OT (does not include IT systems).- Full text: The Cyber/Physical Security Guidelines for Factory Systems(PDF:2,437KB)

- Appendix: Key Considerations for Promoting Smartification(PDF:2,042KB)


Guidelines for Automotive Industry
A framework of countermeasures for automakers and their supply chain companies to address cybersecurity risks unique to the automotive industry.
Includes industry-wide self-evaluation to improve the level of cybersecurity measures for the entire automotive industry and to promote efficient inspections of the level of countermeasures.
JAMA/JAPIA Cybersecurity Guidelines
See the PDF document JAMA/JAPIA Cybersecurity Guidelines (English Version).
The handbook provides detailed explanation of the guidelines is also available on the website.

Guidelines for Space Systems Security
- Summary: Cybersecurity Guidelines for Commercial Space Systems ver. 1.1(PDF:665KB)

- Full Text: Cybersecurity Guidelines for Commercial Space Systems ver. 1.1(PDF:2,846KB)

- Attachment 1: Checklist of Requirements and Measures

- Attachment 2: Correlation between NIST CSF and Specific Measures for Space Systems

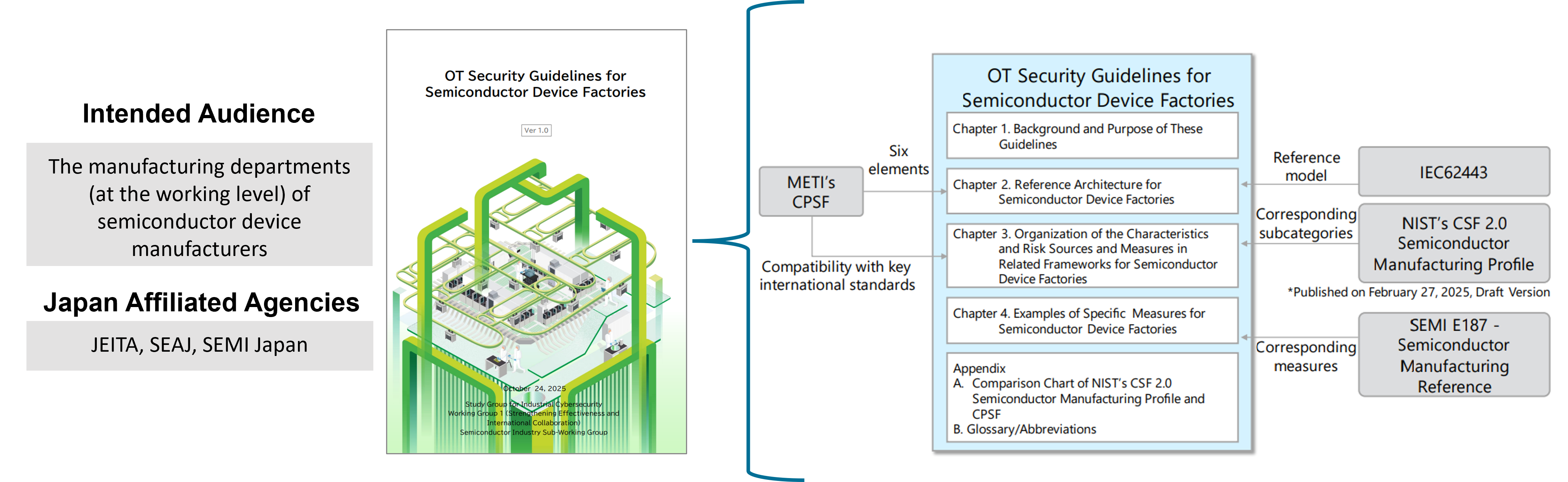
Guidelines for Semiconductor Device Factories
- Summary of OT Security Guidelines for Semiconductor Device Factories: English Version(PDF:3,069KB)

- OT Security Guidelines for Semiconductor Device Factories: English Version(PDF:5,023KB)

Product Security
IoT (Internet of Things)
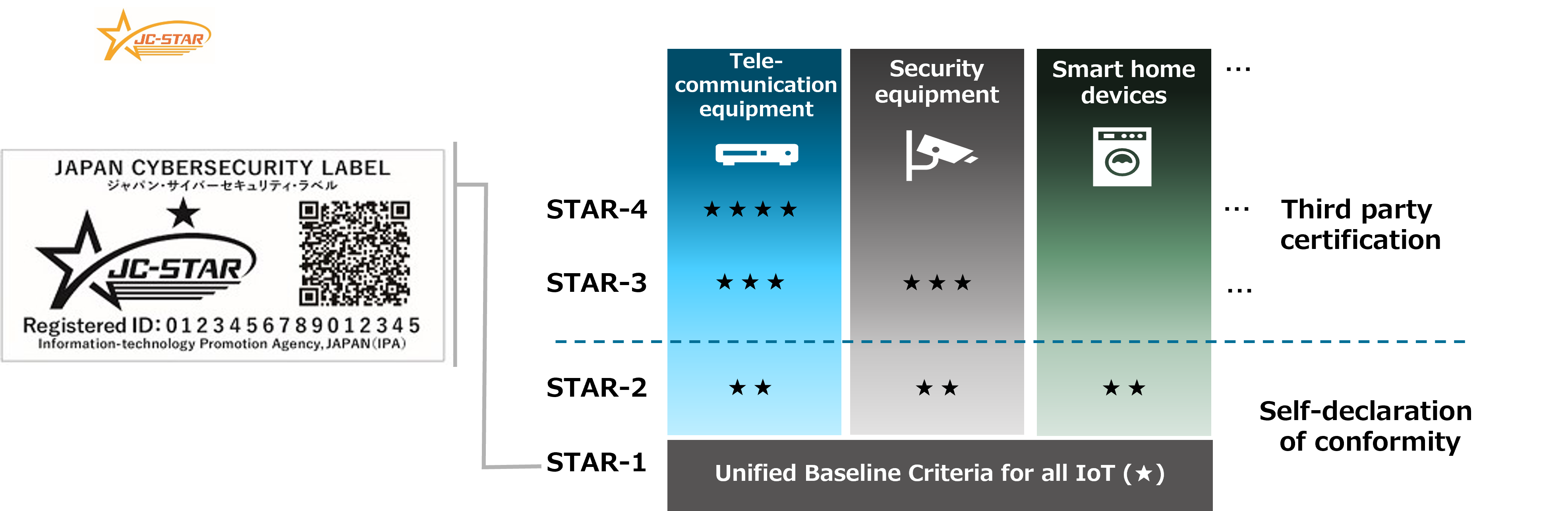
- The Japan Cyber STAR (JC-STAR) is a voluntary Japanese IoT labeling scheme that confirms the conformance of IoT products to original requirements that harmonize with domestic and international standards such as ETSI EN 303 645 and NISTIR 8425.
- Both consumer and industrial IoT products that connect directly or indirectly to the internet using IP are within the scope of this scheme.
- The scheme will have four levels: STAR-1 is a unified baseline to address minimum threats common to all IoT products in scope. The requirements for STAR-2, STAR-3 and STAR-4 will be made per product category. STAR-1 began in March 2025, and STAR-2 and above will begin for certain product categories when ready.
- In addition to promoting secure products in the market, JC-STAR labels will be required in government procurement.
Software Security
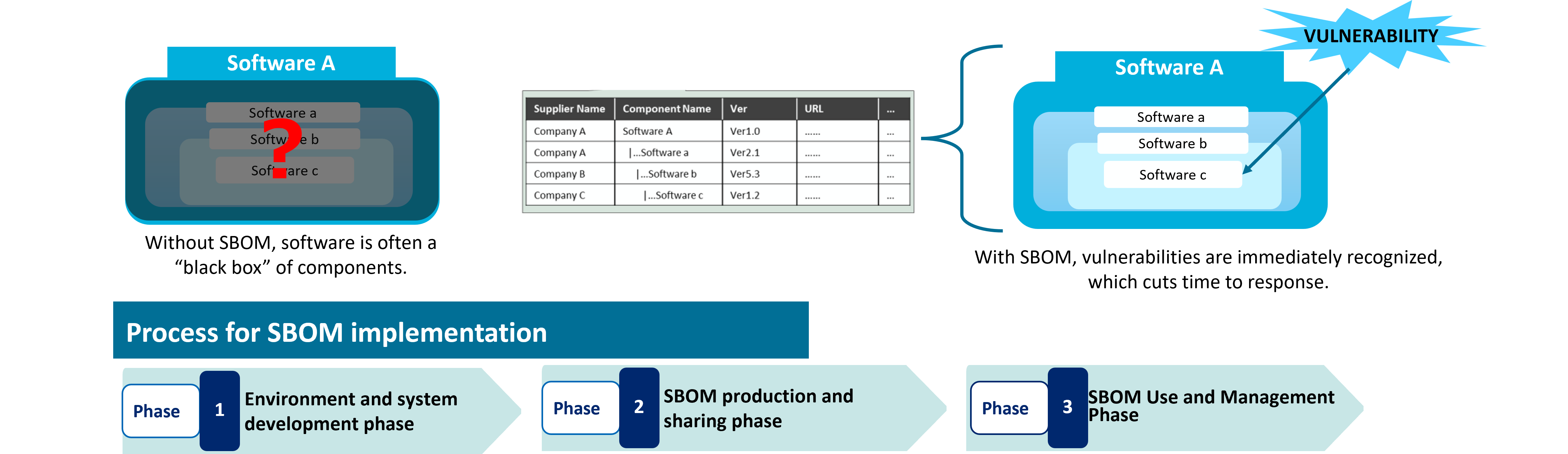
Software Bill of Materials (SBOM)
- As software supply chains become more complex and the use of open-source software (OSS) becomes more common, vulnerability management and license management for software are becoming increasingly important. This can be managed using a Software Bill of Materials (SBOM), a list of software components frequently referred to as a “nutrition label” for software.
- The below guidance provides basic information about SBOM, myths and facts about SBOM, as well as guided actions for introduction to SBOM. This includes guidance on appropriate scope of SBOM implementation, as well as contract models regarding SBOM between a procurer and a supplier.
Guidance ver.2.0 (August 29, 2024)
- Summary: Guidance on Introduction of Software Bill of Materials (SBOM) for Software Management ver.2.0(PDF:732KB)

- Full text: Guidance on Introduction of Software Bill of Materials (SBOM) for Software Management ver.2.0(PDF:3,082KB)

- Appendix: Checklist of actions for the introduction of SBOM ver.2.0(Excel:20KB)

Note: Revisions from ver 1.0
- Approaches to specifying the process for managing vulnerability (Chapter 7)
- Addition of SBOM-compliance model (8. Appendix)
- Addition of SBOM-contract model (9. Appendix)
Guidance ver.1.0 (July 28, 2023)
- Summary: Guidance on Introduction of Software Bill of Materials (SBOM) for Software Management ver.1.0(PDF:285KB)

- Full text: Guidance on Introduction of Software Bill of Materials (SBOM) for Software Management ver.1.0(PDF:1,167KB)

- Appendix: Checklist of actions for the introduction of SBOM ver.1.0(Excel:12KB)

International Guidance on a Shared Vision of Software Bill of Materials (SBOM) for Cybersecurity (September 4, 2025)
Open-source software management
A collection of use case examples on management methods for utilizing open-source software (OSS).
Cyber Skills
Human Resource Development Program
The Industrial Cyber Security Center of Excellence (ICSCoE) under the Information-technology Promotion Agency, Japan (IPA) provides three programs: 1. Core Human Resource Development Program, 2. Programs for Managers, 3. Programs for Practitioners.
JP-US-EU Industrial Control Systems Cybersecurity Week for the Indo-Pacific Region
A one-week training program for the Indo-Pacific region has been held annually by the governments of Japan (METI, ICSCoE IPA), US, and the EU since 2018. Focusing on industrial control system (ICS) cybersecurity, the program aims to improve ICS cybersecurity for critical infrastructure providers, manufacturers, and others in the Indo-Pacific region.

Registered Information Security Specialist (RISS)
The “Registered Information Security Specialist (RISS)” system is a national qualification system for cybersecurity professionals. The RISS system began in October 2016 based on the revised “Act on Facilitation of Information Processing. “
22,845 individuals have been registered as RISS as of October 1, 2024.
Research and Development
Under Construction
Promoting Cyber Industry
Under Construction
Critical Infrastructure:
Gas, Electric power, Petroleum, Credit, Chemical
Under Construction
Underlying Framework:
Cyber/Physical Security Framework
- Summary: Cyber/Physical Security Framework Ver.1.0(PDF:1,373KB)

- Full Text: Cyber/Physical Security Framework Ver.1.0(PDF:4,743KB)

Last updated:2026-01-20